 Managed IT Services
Managed IT Services
Managed Cyber Security Services and IT Compliance
Every business is at risk of a cyber attack, but it’s not just about lost productivity and revenue, it’s about staying compliant and adhering to legal requirements, keeping your users, reputation, and customers secure. It could even prevent you securing lucrative contracts in the future.
With expert guidance, getting your business cyber secure is easier than you think.
Key features of our Managed Cyber Security Services and IT Compliance
Discover how Access IT compliance and cyber security services can support your business in achieving best practice when it comes to meeting compliance and regulatory requirements.
Why choose our managed cyber security solutions and IT compliance services?
Our cyber security services support organisations to achieve best practice when it comes to meeting compliance and regulatory requirements. Our experts help you understand what software you are operating, your users and the access they have to your data, alongside understanding the external threats to your business to help you mitigate the risks.
Fully customisable and scalable to your business requirements, our compliance and cyber security services can be integrated with other security and IT systems making it easier for you to manage overall security and compliance posture.
Our ongoing support provides our customers with training, consulting, and technical support allowing your business to stay up-to-date with the latest security and compliance best practices.

Top benefits of Access Managed Cyber Security
- Regulatory bodies: Our cyber security services support organisations to achieve best practice when it comes to meeting compliance and regulatory requirements
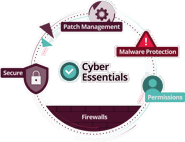
- Cyber Security Essentials: We can support your business to ensure you maintain the highest levels of security and remain complaint with industry leading accreditations.
- Cyber awareness training: Our NCSC certified Cyber Awareness training embeds safe practices across all users in your organisation, reducing risk and putting effective protection in place.
- Device security: Our certified experts will deploy baseline Microsoft 365 data security tools and policies to your users’ devices, including multi-factor authentication to ensure that specific, minimum security levels are met. This will significantly reduce your organisation’s attack surface. Find out more here


Download our Access Managed IT Services Brochure and discover how we can help your business stay on top
Managing every aspect of your IT
We offer an unrivalled set of managed IT services to UK business. With the capability to manage your entire network security, or just a small part to complement your internal expertise. Check out our managed IT support and backup & disaster recovery solutions. Or perhaps you require our cloud expertise to help modernise your business through hosting services or cloud hosting? We’re huge on managed IT security solutions and our Microsoft 365 services, IT compliance and cyber security solutions achieve both the highest levels of security and productivity.
Managed IT Support
Our expert team provides tailored IT support that aligns with your business goals. We can fully manage your IT infrastructure or assist with day-to-day tasks, so you can focus on growing your business.
Virtual Desktops
Work securely from anywhere with our modern Virtual Desktop solutions. We offer application hosting and ensure your business stays protected with top-notch security protocols.
Microsoft 365
Maximise your investment in Microsoft 365 with our specialist team. We provide expert support for migration, licensing, and security to ensure your business is leveraging the full potential of this technology.
Managed IT Security
Our comprehensive security solutions cover compliance, cyber essentials, network, user, and device security. We keep you up to date with industry regulations and protect your business from cyber threats.
Cloud Hosting
Our team provides expert guidance on cloud solutions, including Public, Private, Hybrid, IaaS, and Managed IaaS. We can help you leverage the latest cloud technologies and access tools like The Access Cloud and Microsoft Azure.
Disaster Recovery
Be prepared for the unexpected with our comprehensive disaster recovery plan. We ensure minimal downtime and quick recovery of critical data and systems in the event of a disaster.
Blog Spotlight: Managed IT Services
Read our latest blogs on all things managed IT services covering key industry questions and trends.
Managed IT Services NewsIT Compliance and Cyber Security Services FAQs
What are the most common compliance requirements for businesses?
Compliance requirements can vary based on a number of factors, including industry, size of your the business, and location. However, here are some of the most common compliance requirements that businesses need to consider:
- Data Protection and Privacy: Many businesses are required to comply with data protection and privacy laws such as the General Data Protection Regulation (GDPR) in the European Union or the California Consumer Privacy Act (CCPA) in the United States.
- Cyber security compliance: These standards vary depending on the policies and regulations in place, but typically encompass areas such as data encryption, authentication protocols, vulnerability scanning and incident response planning. By assessing potential threats and vulnerabilities and implementing protective measures accordingly, organisations can mitigate the chance of cyber crime attempts against their company’s sensitive data.
- Tax Compliance: Businesses are required to comply with a variety of tax laws and regulations, including federal, state, and local taxes. This can include income tax, payroll tax, sales tax, and other taxes.
- Financial Reporting: Publicly traded companies must comply with financial reporting regulations such as the Sarbanes-Oxley Act (SOX) in the United States and the International Financial Reporting Standards (IFRS) in many countries.
- Employment and Labor Laws: Businesses must comply with a range of laws and regulations that govern the employment relationship, including minimum wage, overtime, equal employment opportunity, discrimination, harassment, and workplace safety.
- Environmental Regulations: Businesses must comply with environmental regulations that govern things like air and water quality, waste management, and hazardous materials handling.
- Health and Safety Regulations: Businesses must comply with regulations that protect the health and safety of employees and the public. This can include workplace safety standards and regulations governing the production and distribution of food, drugs, and medical devices.
- Licensing and Permits: Many businesses are required to obtain licenses and permits to operate legally in their industry and location. This can include business licenses, professional licenses, and permits for specific activities like building construction or alcohol sales.
What is cyber security compliance?
Cybersecurity compliance is an essential aspect of protecting a business from the increasing number of cyber threats. There are various cybersecurity compliance requirements that businesses must consider, including:
- PCI DSS: Payment Card Industry Data Security Standard (PCI DSS) compliance is required for businesses that process, transmit, or store credit card data. It involves following specific requirements related to data protection and secure handling of credit card information.
- GDPR: The General Data Protection Regulation (GDPR) is a European Union regulation that applies to businesses that process or handle personal data of EU citizens. GDPR compliance involves following specific data protection and privacy requirements, including data subject rights and breach notification.
- SOC 2: Service Organisation Control (SOC) 2 compliance is a standard for companies that provide services to other businesses. SOC 2 involves following specific security and privacy controls to protect the data and systems of the business's customers.
- ISO 27001: ISO 27001 is an international standard that provides a framework for information security management systems (ISMS). ISO 27001 compliance involves implementing a systematic approach to managing and protecting sensitive information.
- ICO: The ICO is the independent supervisory authority for data protection in the UK, with a mission to uphold information rights for the public in the digital age.
- SRA: The Solicitors Regulation Authority (SRA) Standards and Regulations set out the high professional standards expected of the solicitors, lawyers and businesses it regulates.
How can I ensure my business is compliant with cyber security regulations?
Compliance with cyber security regulations is critical to running a successful business. To ensure your business is compliant, it is important to have appropriate policies and procedures in place, as well as training programs for your employees. This can include access control measures, malware detection tests, firewalls and encryption standards. Additionally, consider investing in a managed security service that can monitor and audit your systems on a regular basis for any potential vulnerabilities or threats. Ensuring your business is compliant with cyber security regulations can help you protect both valuable company assets and customer data, and provide peace of mind to those who entrust their information with you.
What are the consequences of non-compliance?
Non-compliance can have a variety of consequences, from financial to criminal. Failing to comply with laws, regulations and protocols can lead to fines for businesses and individuals, or even imprisonment for acts such as tax evasion. People who are employed in organisations that are found not to be in compliance may put their jobs at risk by being associated with such behaviour. Non-compliance can also result in lost revenue due to being unable to take part in certain activities or access investments or resources. The cost of remediating any mistakes caused by non-compliance can often be times greater than the cost of preventing them in the first place.
How can I create a cyber security plan for my business?
Creating a cyber security plan for your business is vital in today's world. To ensure that you have the utmost level of data protection, start by identifying potential threats like viruses, hackers, and other malicious activity. Once these are identified, develop an appropriate action plan to mitigate risks. Educating staff on cyber threats and implementing strong password protocols are simple yet necessary steps to take for protecting your digital assets. Having the right technology in place such as firewalls and anti-virus software can also be beneficial for safeguarding your network. The Access Group can support your business in creating a comprehensive cyber security plan which will decrease the chances of harm and allow your business operations to continue running smoothly in the case of a cyber attack.
How often should I update my cyber security plan?
Frequently changing online environments and increased levels of digital threats mean that updating your cyber security plan should be part of your regular to-do list. No matter what size business you operate, understanding the latest cyber threats and evaluating the effectiveness of strategies put in place will not only maximise your data security but is also essential for long-term success in a quickly evolving tech landscape. To stay ahead of hackers, it is recommended to regularly review and update your existing policies or create new ones if necessary. You should also take the time to review potential vulnerabilities on a monthly or even weekly basis as hackers are continuously refining their tactics - so you need to remain vigilant as well!
What are the common cyber security threats?
Cyber security threats are increasing on a daily basis, making it integral for individuals and companies to be aware of the risks they face. Hacking, phishing, ransomware, malvertising and DoS (denial of service) attacks all threaten both individual users and businesses alike. Through hacking, attackers can gain access to sensitive data or personal accounts without permission; phishing scams target users in an attempt to get them to divulge information willingly; malvertising tricks unsuspecting users into clicking malicious links; finally, DoS attacks aim to overwhelm networks with fake traffic, hoping to cause access outages and slow service. All of these cyber security threats have one thing in common: the intent to undermine the security of online systems. Having the knowledge of these dangers is invaluable in protecting your digital assets from falling victim to a cyber criminal.
How can I protect my business from cyber attacks?
Protecting your business from cyber attacks should be a top priority for any business owner, especially with the increasing frequency and sophistication of cyber crime. Investing in strong security protocols such as firewalls, secure passwords and encryption technology are essential steps to keeping your data safe. Keeping up with software patches and ensuring third-party vendors have stringent security measures in place can also help protect your business from falling victim to malicious actors on the web. Moreover, educating staff on best practices when it comes to online safety can reduce potential risks associated with employee negligence. When it comes to cyber security, an ounce of prevention is worth a pound of cure.
What should I do if my business is the victim of a cyber attack?
A cyber attack can be a devastating blow to any business. If your business has fallen victim to a cyber attack, you must act quickly and decisively in order to minimise the damage and prevent similar attacks in the future. The first step you should take is contacting the authorities, especially if there is a chance that sensitive data has been compromised. Contacting law enforcement officials will ensure that the necessary steps are taken to identify and prosecute the individual responsible for the attack. Additionally, you should invest in insurance plans which cover potential damages from cyber attacks, as well as implementing additional security systems to prevent future targeted assaults. Lastly, make sure all of your employees are aware of proper cyber security practices so that everyone at your business takes an active role in avoiding these kinds of incidents. A cyber attack can cause serious disruption for any business, but with the right response it can be successfully handled.
Who can I contact for help with compliance and cyber security for my business?
When it comes to the critical task of protecting your business from the risks associated with compliance and cyber security, the Access Group provides the expertise and experience you need. Their comprehensive offerings include a range of services for small- to medium-sized businesses, from detailed risk assessments that help identify potential weaknesses to proactive monitoring and training programs designed to protect against the ever-evolving threat landscape. With over 30 years of experience in the security industry, the Access Group has the knowledge base and resources needed to provide the highest level of protection for your business. Contact the Access Group today to start developing a plan tailored to your organisation's needs.

 AU & NZ
AU & NZ
 SG
SG
 MY
MY
 US
US
 IE
IE












